- 更新:2020-05-05 16:37:12
- 首发:2018-11-14 19:22:21
- 教程
- 9295
公益SSL证书机构Let’s Encrypt从2018-03-13起开始支持通配符证书。通配符证书必须通过DDNS添加TXT记录验证域名所属权。
照 certbot官网安装certbot。
安装DNS插件
cerbot支持很多DNS插件,例如:certbot-dns-cloudflare certbot-dns-cloudxns certbot-dns-digitalocean certbot-dns-dnsimple certbot-dns-dnsmadeeasy certbot-dns-google certbot-dns-linode certbot-dns-luadns certbot-dns-nsone certbot-dns-ovh certbot-dns-rfc2136 certbot-dns-route53 ...这里以DNSPOD(腾讯云域名默认DNS)为例:
git clone https://github.com/tengattack/certbot-dns-dnspod cd certbot-dns-dnspod sudo python setup.py installIf you are using
certbot-auto, you should runvirtualenvfirst:# CentOS 7 virtualenv --no-site-packages --python "python2.7" "/opt/eff.org/certbot/venv" /opt/eff.org/certbot/venv/bin/python2.7 setup.py install安装完成后,到DNSPod控制台生成
API Token,并保存在配置文件/path/credentials.ini。certbot_dns_dnspod:dns_dnspod_api_id = 12345 certbot_dns_dnspod:dns_dnspod_api_token = 1234567890abcdef1234567890abcdef赋予相应权限:
chmod 600 /root/credentials.ini执行生成指令
certbot certonly -a certbot-dns-dnspod:dns-dnspod --certbot-dns-dnspod:dns-dnspod-credentials /root/credentials.ini -d xxx.com -d "*.xxx.com" --server https://acme-v02.api.letsencrypt.org/directory生成的证书默认在
/etc/letsencrypt/live/xxx.com/目录。配置Nginx
server { listen 80; server_name *.abc.com; charset utf-8; autoindex off; location / { return 301 https://$host$request_uri; } } server { listen 443; server_name *.abc.com; ssl on; ssl_certificate /etc/letsencrypt/live/abc.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/abc.com/privkey.pem; ssl_session_timeout 5m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE; ssl_prefer_server_ciphers on; charset utf-8; autoindex off; index index.html index.htm; location / { proxy_http_version 1.1; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_set_header X-NginX-Proxy true; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; proxy_pass http://127.0.0.1:8888$request_uri; proxy_redirect off; } }
设定定时更新(每次申请到的证书有效期三个月)
crontab -e 0 0 1 * * python -c 'import random; import time; time.sleep(random.random() * 3600)' && certbot renew && nginx -s reload表示每月自动执行续期脚本并热重启nginx。
测试自动续订:
sudo certbot renew --dry-run
参考文章:
https://latlonworld.com/article/free-wildcard-ssl-with-lets-encrypt.html
https://latlonworld.com/article/free-ssl-with-lets-encrypt.html
----- 2018年12月31日20:35:35 更新
如果CentOS出现ImportError: 'pyOpenSSL' module missing required functionality报错,解决方案:
需要到该FTP中寻找对应版本的pyOpenSSL模块安装,例如:
rpm --query centos-release # centos-release-7-6.1810.2.el7.centos.x86_64
sudo yum remove certbot
wget ftp://ftp.muug.mb.ca/mirror/centos/7.6.1810/cloud/x86_64/openstack-rocky/python2-pyOpenSSL-17.3.0-3.el7.noarch.rpm
sudo rpm -Uvh python2-pyOpenSSL-17.3.0-3.el7.noarch.rpm
sudo yum install certbot
certbot renew # OK
更多详情:https://github.com/certbot/certbot/issues/4514
推荐
另外一种获取通配符证书的方案:https://github.com/Neilpang/acme.sh
----- 2019年11月15日16:00:45 更新
基于Docker:https://github.com/JrCs/docker-letsencrypt-nginx-proxy-companion
示例:
docker run --detach \
--name nginx-proxy \
--publish 80:80 \
--publish 443:443 \
--volume /etc/nginx/certs \
--volume /etc/nginx/vhost.d \
--volume /usr/share/nginx/html \
--volume /var/run/docker.sock:/tmp/docker.sock:ro \
jwilder/nginx-proxy
docker run --detach \
--name nginx-proxy-letsencrypt \
--volumes-from nginx-proxy \
--volume /var/run/docker.sock:/var/run/docker.sock:ro \
--env "DEFAULT_EMAIL=您的邮箱" \
jrcs/letsencrypt-nginx-proxy-companion
docker run -itd -m 512m \
--restart=always \
--name front \
-v `pwd`/dist:/usr/share/nginx/html \
--env "VIRTUAL_HOST=example.com" \
--env "LETSENCRYPT_HOST=example.com" \
nginx
这个方式便捷高效,比较稳定。基于Let's Encrypt且可以用于Docker Compose、K8S的方案目前Github上有很多。
----- 2020年03月07日23:33:15 更新
更详细的配置请参考博文Docker搭配免费SSL证书 。
暂无内容




老师你好,我希望能用一个openwrt路由器实现IPv4和IPv6的桥接,请问我该如何实现?我尝试了直接新增dhcpv6的接口,但是效果不甚理想(无法成功获取公网的ipv6,但是直连上级路由的其他设备是可以获取公网的ipv6地)
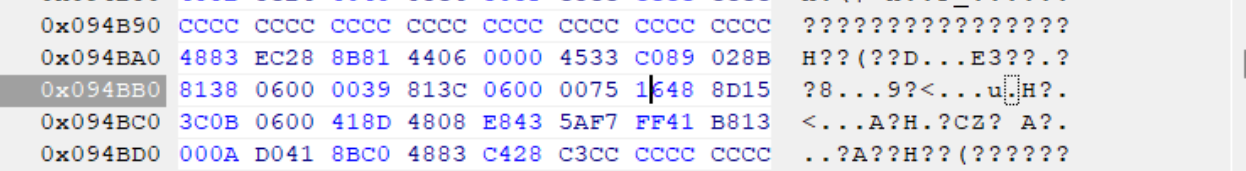你好
,为什么我这里是0039 813C 0600 0075 16xx xx xx,只有前6组是相同的,博客中要前8位相同,这个不同能不能照着修改呢?我系统版本是Win1124H2
大神你好,win11专业版24h2最新版26100.2033,文件如何修改?谢谢
win11专业版24h2最新版26100.2033,Windows Feature Experience Pack 1000.26100.23.0。C:\Windows\System32\termsrv.dll系统自带的这个文件,39 81 3C 06 00 00 0F 85 XX XX XX XX 替换为 B8 00 01 00 00 89 81 38 06 00 00 90。仍然无法远程连接。原来是win11 21h2系统,是可以远程链接的。共享1个主机,2个显示器,2套键鼠,各自独立操作 各自不同的账号,不同的桌面环境。
博主,win11专业版24h2最新版,C:\Windows\System32\termsrv.dll系统自带的这个文件,找不到应该修改哪个字段。我的微信:一三五73二五九五00,谢谢